According to recent reports, Microsoft edged out Facebook to become the brand most impersonated by phishers in the first half of 2022. The day after I read this news update, I received the following phishing email:
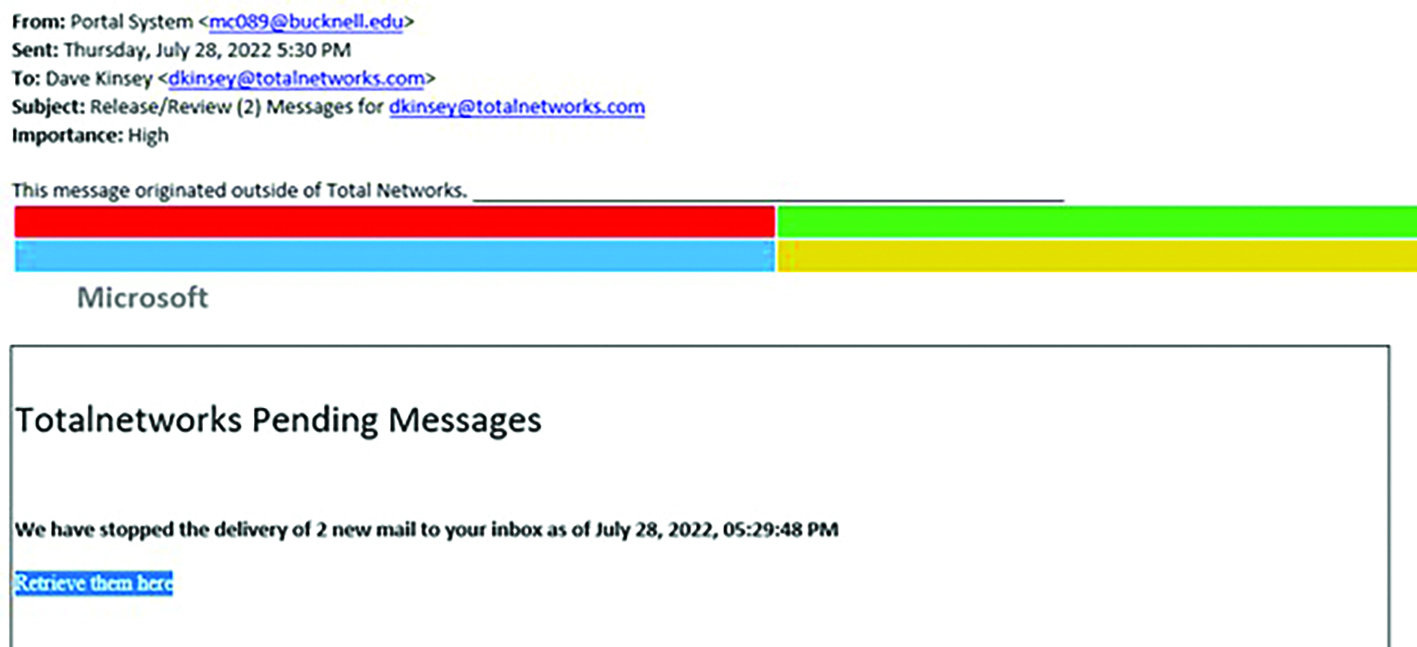
We consume and trust the products and services of Microsoft and many other brands. Bad actors prey on that trust.
The above message is blatantly fake. It claims to come from bucknell.edu with whom I have zero affiliation. The High importance flag is also suspicious. Phishers often project a sense of urgency. A high importance flag is common for phishing emails and less common for legitimate system-generated messages, which this message purports to be. Th is message should have ideally been filtered out by our email security system (a.k.a. “spam filter”), but it was not. No system is perfect. Bad actors try varied creative attempts to get their messages through and some invariably succeed.
Had I clicked on the link in the message, I am fortunately protected by additional layers that likely would have disallowed following the link. First, the link was rewritten by the email filter as the message passed through it. We have our email security configured to automatically perform additional screening of emailed links when they are clicked on. Second, our network has redundant native web traffic scanning and filtering provided by a different security company. We have many other layers of protection as well.
Still, I would never intentionally test these defenses by simply clicking on a real phishing message. User education is an important security layer, and I am too well-informed to click on such a link. Defenses need to succeed every time. Bad actors need only succeed once. Therefore, it is essential to have several redundant security layers.
So, what should you do to protect yourself against phishing attacks in 2022?
First, ensure that your IT has strong technical controls in place. These technical controls must include many layers of defense such as strong email filtering, URL rewriting in the email filtering, IDS/IPS systems, web filtering, up-to-date system patching, strong endpoint protection, SOC and SEIM protection, strong passwords, and multifactor authentication.
Additionally, train your employees to be wary of suspicious emails. Phishing messages may purport to come from friends, acquaintances, your clients, or suppliers. Or they may appear to come from trusted brands like Microsoft , Amazon, FedEx, UPS, your mobile phone carrier, or a bank. The email will be intentionally deceptive and may be very convincing.
The best way to defend against such tricky attacks is to regularly conduct simulated phishing email campaigns. Pretend to be devious for a good cause. Simulated phishing emails that we send our clients are generally more convincing than the above example. We try to condition people to be diligently skeptical about every email. Whenever we trick someone into clicking a link, it is recorded so we can a follow-up on that. If they are fooled into providing login credentials, they are immediately redirected to online training. We review reports and monitor the progress to confirm that fewer people are fooled over time. Nobody wants to get caught clicking on something that they shouldn’t have, so they automatically change their behavior for the better. And in the rare cases that someone repeatedly gets fooled, we provide some extra one-on-one training.
Phishing is, by far, the source of most successful cyber-attacks including ransomware attacks. It is successful because there is always someone willing to click on that link that they shouldn’t. Let’s do everything we can to make sure that next click isn’t coming from you or someone in your organization.









