Thus far, 2023 has been a bad year for law firms and cyberattacks. Quinn Emanuel, K&L Gates, Proskauer and Kirkland & Ellis have all been hit hard. The number of small to mid-sized firms that have been hit are countless.
I sat down with a number of industry professionals to get their best advice on preventing law firm cyberattacks.
What Anyone Can Do About Cybersecurity
Justin Daniels is a cybersecurity partner at Baker Donelson and and faculty at IANS Research. He had a great deal to offer on the subject of cybersecurity, including where firms should start.
“Well, number one is you have to have a mindset shift. Law firm leadership needs to realize that they have a duty of confidentiality to clients, and that duty of confidentiality extends to protecting their data from unauthorized access. So, management has to be on board and fully committed to taking effective measures.
“A good place for them to start is the National Institute for Standards and Technology, the Cybersecurity Framework aka NIST CSF. They break cybersecurity down into five categories: Identify, Protect, Detect, Respond and Resilience.
“Regarding the first two categories, it’s easy to identify what are the crowned jewels at law firms, that cyberattackers will seek to gain or make inaccessible – client data. So that’s where firms will need to focus their protective measures.”
Training
Mike Caralis, VP of business markets for Verizon, North America, says the single most important step any organization can take toward improving their cybersecurity is training.
“You can have the most robust cybersecurity tools, but your biggest threat may be sitting in your office. Human error plays a significant role (74%) in breaches. This means that even the most cybersecurity aware employees may make a mistake from time to time. Conducting cybersecurity training regularly will improve awareness around common cyberthreats (e.g., phishing, harmful websites, and unsafe downloads). This includes training employees on the dangers of mobile phishing (smishing) as users are 6-10 times more likely to fall victim to SMS phishing than email attacks.”
For example, a typical employee might view this email I received and simply click on the link, without noticing that the sender’s address does not end with docusign.com. Once they do, they could open malware without even knowing it.
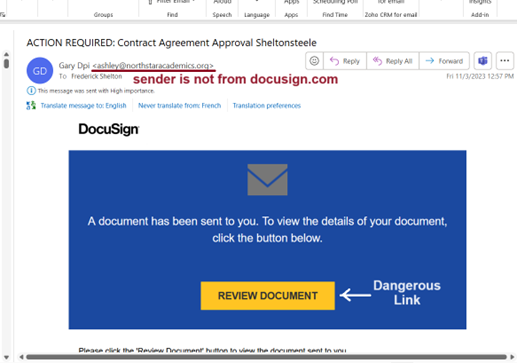
But if they are regularly trained to look for the signs that something is amiss, they’re less likely to open their firm to attack.
Mr. Caralis strongly recommends that firms go beyond just training though. He says that law firms should have strong and comprehensive cybersecurity policies in place.
“Defining an acceptable use policy (AUP) can set the standard on how devices are used and protected. We already know that human error can play a big factor with breaches, so defining what cybersecurity policies should be in place is crucial. It’s equally crucial to take action and put those policies to work! The policy should address common cybersecurity vulnerabilities (e.g., weak passwords, phishing attempts, keeping software up to date, securing Wi-Fi, BYOD risks, etc.).”
Multi-Factor Authentication
Both Justin Daniels and Mike Caralis are huge proponents of requiring multi-factor authentication. Mr. Daniels shared actions he’s taking personally.
“I’m investing in the better license for Microsoft that allows you to initiate multifactor authentication, preferably one that’s token based, not SMS text,” Daniels stated.
Caralis was adamant in this position, as well.
“Doubling down on a multi-factor authentication (MFA) policy is a must. Forty-nine percent of cyber-attacks involve stolen credentials and think about what that could mean for your law firm. Having an MFA adds an additional layer of protection if your credentials are stolen, making it significantly harder for the threat actor to get into your network.”
Detection & Reporting
Once a firm has been breached, the most important factor then becomes detection. With malware attacks that prevents the firm from being able to access files, this becomes obvious. But Trojan Horses and other types of attacks can go undetected for a long time. Whatever the case, when your firm has been hacked, you have an ethical obligation to immediately report it to your clients.
Imagine how a client would react if they discovered that the opposing counsel in the litigation, could see every file, every email, every strategy etc. in their case. Imagine how much worse it would be, if the firm knew they’d been breached but didn’t tell their clients for over a year! That’s exactly what a class action lawsuit is claiming that Hill, Farrer & Burrill did during the last 15 months.
If your firm gets breached, your clients won’t like it but if Kirkland & Ellis’ clients can handle that kind of bad news, so can yours. Do not try to hide it. Report it as soon as you have an assessment of what happened.
Response & Recover
Smart companies and firms have a plan in place to deal with cyberattacks. They know what they’re going to do, long before it happens. Caralis described this in easy-to-understand terms.
“Once you have been breached, you need to act quickly, with the goal of having an incident response plan already created. An incident response plans objective is to limit the damage a threat actor can do, and to reduce the downtime. It involves having the right tools, being able to determine the scope of the breach, containing the breach, remove the threat, and then recover. “
Protection Outside the Office
Attorneys often use their laptops at airports and hotels. Virtually every attorney I know, works from home at least some of the time. Thus, they are outside the security offered within the confines of their offices. But according to the American Bar Association’s 2022 Cybersecurity Survey only 59% of law firms report having policies governing secure technology use for remote access.
Rich Kanadjian, the encrypted business manager at Kingston Technologies finds that highly problematic – especially because his company sells a solution.
“A solution that more and more firms and lawyers are turning to is hardware-encrypted, password-protected flash drives. These drives are ‘air-gapped’ storage and a cloud in your pocket that can be accessed, used, and secured without an internet connection and there is no concern that they will be hacked or decrypted if lost or stolen, as each drive has a hardware microprocessor built directly into the device and can safely be accessed without needing to connect to a public cloud to retrieve a needed file. Each drive is its own secure ecosystem that solely depends on a strong password to access the data, making them invulnerable to brute force attacks.”
Those drives are ideal but what about someone who works from home on a regular basis? Hackers can cut through consumer routers and into the Wi-Fi networks with relative ease. A friend of mine did a penetration test (wherein, they discover how hard it will be to break through a company’s defenses) for a bank. Instead of emails, links etc. he attacked the Wi-Fi itself and within one minute, reported to the bank manager that he had access to everything. The manager was shocked.
Let There Be Light!
There is now a new type of technology that eliminates any chance of hackers accessing the Wi-Fi of an attorney working from home: “Li-Fi”. Instead of using radio waves (which are hackable), this amazing new technology uses light waves. I spoke with Mike Fasulo, the COO and co-founder of PhotonFi, the only company in the United States that offers LiFi. Mike actually retired as the head of Sony, North America and then came out of retirement, specifically because he was so impressed with this new technology. He told me that Li-Fi offers three attributes that will make it a game-changer:
- Security – You can’t hack or jam Li-Fi because it uses light-based connectivity and therefore no radio wave to hack or jam. This is 100% completely secure to the level of military grade. Your in-office communications will stay secure, immune to inside or outside eavesdropping.
- Stability – You can’t overwhelm it with too many users (with Wi-Fi the more users on the system the slower it becomes, due to degradation). With PhotonFi’s LiFi products each user is discrete and will experience a stable and consistent upload and download speed. Obviously, the ISP or inbound pipe will have to be initially delivering that level of speed.
- Latency – Latency is the delay between the time the signal is sent from the router or source, and the time it is received at the computer. Li-Fi is up to 300x better than Wi-Fi. A high or uncontrollable latency makes audio and video conferencing difficult, and virtually eliminates access to time-sensitive applications.
Do Something!
Cybersecurity is no longer an issue wherein procrastination is excusable. If your law firm isn’t taking cybersecurity precautions, you aren’t worthy of the trust of your clients and you could be the subject of a lawsuit. You can start out with actions that are free and easy, like training your employees, setting clear cybersecurity policies in place and using multi-factor authentication. If your clients are large companies, tech companies, banks, the DoD etc. you’ll want to take more robust measures. But when it comes to cybersecurity, it’s time to do something.









